Unlocking the secrets of Docker networking can be a game-changer for any developer. Imagine effortlessly connecting your containers with your host system and each other, streamlining your development process like never before. In this blog, we won’t just scratch the surface by showing you how to create or delete containers. Instead, we’ll dive deep into the fascinating world of Docker networking. By the end, you’ll know how Docker networks function and discover powerful ways to apply this knowledge to your projects. Ready to revolutionize your workflow? Let’s demystify Docker networking together! Plus, stick around for some top-notch resources to expand your learning even further.
Overview
Container networking is the backbone of communication between containers and the host machine. By default, containers have networking enabled, allowing them to interact seamlessly. Each container perceives a network interface with an IP address, gateway, routing table, DNS services, and other essential networking details.
In this article, we will delve into three key concepts of Docker networking:
- Isolation of the Docker Network: Understanding how Docker ensures each container operates within its secure network space.
- Communication Between Docker Containers: Exploring the mechanisms that allow containers to communicate with each other.
- Network Drivers and Use Cases: Examining different network drivers and their practical applications in real-world scenarios.
Isolation of the docker network
Linux introduced the namespace that Docker uses in 2002. The namespace isolates different processes, such that one set of processes shares one set of resources, and another shares different resources. Docker itself creates a set of namespaces in your local machine. Bingo!!
When docker creates a container, it has a separate isolated networking system with an IP address, a gateway, a routing table, a DNS service, etc. This isolation is called network namespace isolation.
How docker containers communicate
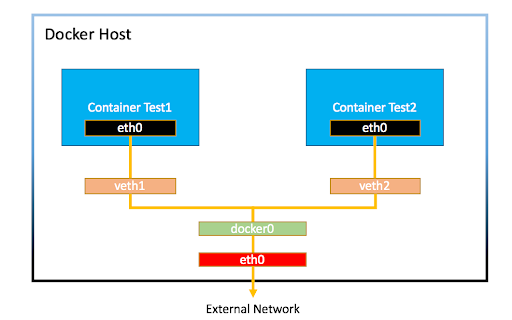
Docker creates a virtual ethernet interface for each container. This interface, called veth, creates a pipe between the host machine and the container networking namespace.
Example:
Docker creates a bridge network called docker0. When we start a container, Docker connects the virtual Ethernet interface to the bridge network. This bridge network enables communication between containers on the same host.
Network driver and some use case
Several types of drivers exist in Docker. Now, I will discuss some of them.
- Bridge: This is the default driver for docker and the docker0 network. The bridge driver communicates between containers on the same host machine. A bridge device is a link layer device used to forward traffic between network segments. In docker, the bridge is a software bridge that allows communication containers on the same bridge network. It provides isolation from multiple containers’ communication on multiple bridge networks. It has its network namespace, including IP address, subnet, etc.
- Host: This is another type of driver that exists on docker. When the network mode is host, the containers use the host network namespace contrary to the bridge driver. Suppose you run a container on port 80 on the host machine with network mode host. In that case, docker will expose the application directly to the 80 port.
- Overlay: In my previous two drivers, I discussed two scenarios of Docker container communication. After that, we have another point of discussion: How can Docker containers on different hosts communicate? Then, there comes the Docker overlay driver. This driver is used to transmit two containers running on two different hosts.
- None: This driver prevents communication between containers. It is useful when you need fully isolated Docker containers.
I hope I have given you some thought to how docker containers communicate with each other and the host machine. Happy reading