Welcome to the world of Linux, where everything is a file, and every file has a story to tell. Today, we will embark on a journey through the Linux file system and uncover the mysteries of file permissions. Whether you’re a seasoned sysadmin or a curious newbie, this guide will help you understand the structure and security of your Linux environment with some catchy examples along the way. So, grab your favorite beverage, sit back, and let’s get started!
Chapter 1: The Linux File System Hierarchy
The Root of All Things: ‘/’
In Linux, the file system begins at the root directory, represented by a simple /. Think of this as the trunk of a massive tree, from which all other directories (branches) grow. Here are some of the critical directories you’ll find at the root level:
- /bin: This is where you’ll find essential binary executables. For instance, commands like ls, cp, and mv live here.
- /boot: Contains the files needed to boot your Linux system, including the kernel.
- /dev: Short for devices, this directory holds files representing hardware devices.
- /etc: The epicenter of configuration files and scripts.
- /home: A personal haven for every user. Each user gets a subdirectory here, like /home/alice.
- /lib: Shared libraries and kernel modules.
- /mnt: Temporary mount points for filesystems.
- /opt: Optional software packages.
- /proc: A virtual filesystem that provides a mechanism to access kernel data structures.
- /root: The home directory for the root user.
- /sbin: System binaries remain accessible only to the system administrator.
- /tmp: Temporary files.
- /usr: User binaries and applications.
- /var: Variable data files like logs.
Example: Navigating the Tree
Imagine you’re Hasan, a new user of a Linux system. You want to explore your home directory. Here’s how you can do it:
cd /home/hasan
ls
You’ll see all the files and subdirectories in your personal space. It’s like opening the door to your digital room!
Chapter 2: Understanding File Permissions
Linux file permissions are crucial for system security and management. Here’s a quick overview to help you understand how they work
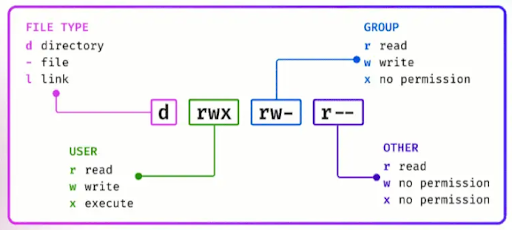
The Triad of Permissions
In Linux, every file and directory has permissions to determine who can do what with them. These permissions are categorized into Read, Write, and Execute.
- Read (r): Allows reading the contents of a file or listing the contents of a directory.
- Write (w): Allows modifying a file or directory.
- Execute (x): This option allows you to execute a file (if it’s a script or a program) or access a directory and its contents.
Who Gets What?
Assign permissions to three types of users:
- Owner: The user who owns the file.
- Group: A set of users who share the same permissions.
- Others: Everyone else.
The Permission String
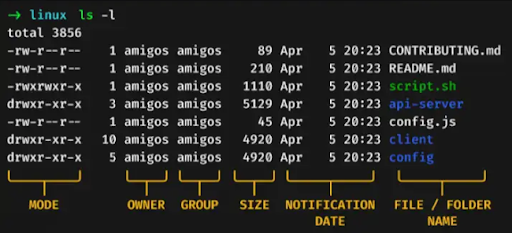
The permission string is a sequence of ten characters, such as -rwxr-xr–, which can be broken down as follows:
- The first character indicates the file type (– for a regular file, d for a directory).
- The following three characters (rwx) are the owner’s permissions.
- The following three (r-x) are the group’s permissions.
- The last three (r–) are for others.
Example: Decoding Permissions
Consider a file with the following permissions:
-rwxr-xr--
- The owner can read, write, and execute (rwx).
- The group can read and execute (r-x).
- Others can only read (r–).
Changing Permissions: The ‘chmod’ Command
You can change file permissions using the chmod command. There are two ways to do this: symbolic mode and numeric mode.
Symbolic Mode
In symbolic mode, you use letters to represent permissions and operators to add or remove them.
User Types
- u: User (file owner)
- g: Group (file’s group)
- o: Others (everyone else)
- a: All (user, group, and others)
Operations
- +: Add a permission
- –: Remove a permission
- =: Set exact permissions, removing others
Permission Types
- r: Read
- w: Write
- x: Execute
Examples of Symbolic Mode
Add execute permission for the user:
chmod u+x file.txt
Remove write permission for the group:
chmod g-w file.txt
Setting Exact (=) Permissions. Set read and write for the user, read for the group, and no permissions for others:
chmod u=rw,g=r,o= file.txt
Combine multiple changes: add read permission for the group and others, and remove ‘execute’ permission for the user.
chmod g+r,o+r,u-x file.txt
Numeric Mode
In numeric mode, you use a three-digit number to set permissions. Each digit represents a set of permissions:
- Read (r) = 4
- Write (w) = 2
- Execute (x) = 1
Add these values to get the desired permissions. For example, 755 means:
- Owner: rwx (4+2+1 = 7)
- Group: r-x (4+0+1 = 5)
- Others: r-x (4+0+1 = 5)
chmod 755 file.txt
Example: Setting Permissions
Imagine you have a script run.sh that you want to make executable by everyone:
chmod 755 run.sh
Everyone can run the script here, but only you can modify it.
Chapter 3: Ownership and Groups
The chown Command
The chown command changes the owner of a file. Here’s an example:
chown hasan file.txt
This command makes Hasan the owner of file.txt.
The chgrp Command
The chgrp command changes the group of a file:
chgrp staff file.txt
This command assigns the file to the staff group.
Changing Ownership and Group
Suppose Mishu wants to transfer ownership of project.zip to Hasan and change its group to developers:
chown hasan project.zip
chgrp developers project.zip
Now Hasan owns project.zip, which is part of the developers group.
Chapter 4: Fun with Permissions
Making a Secret Directory
Let’s say you want to create a secret directory only you can access. Here’s how:
mkdir secret
chmod 700 secret
- 700 means only the owner can read, write, and execute.
Creating a Shared Directory
Suppose you’re working on a group project and need a shared directory where everyone can add and edit files:
mkdir shared
chmod 770 shared
- 770 means the owner and group can read, write, and execute, but others have no access.
Example: Permission Pitfalls
Imagine you accidentally made a sensitive file readable by everyone:
chmod 644 sensitive.txt
- 644 means the owner can read and write, but everyone else can read.
To fix this, you need to restrict access:
chmod 600 sensitive.txt
600 means only the owner can read and write.
Conclusion
And there you have it — a comprehensive, fun-filled guide to the Linux file system and permissions. By now, you should feel more confident navigating directories and managing file permissions like a pro. Understanding and managing file permissions is vital for maintaining system security and ensuring proper access control. Regularly check and update permissions to keep your Linux environment secure.
Stay tuned for more exciting Linux adventures, and until next time, happy computing!
Stay classy!